FAQs
Following are the most common questions, along with answers from Ingate’s Help
Desk. If the question you have is not answered below, or if you need
additional information, please contact us via e-mail at support@ingate.com.
License/licensing Problems
-
Will the unit reboot when I apply the license?
-
I applied the license key to the wrong unit serial - can I change it? a.k.a. Can I migrate a license from my Ingate XX to my VM?
-
I lost the license file but have not applied it yet - can I get a new one?
-
Does the Ingate support video and would there be any licensing and capacity implications we need to consider?
Will the unit reboot when I apply the license?
The nature of most licenses will require that the unit restarts/reboots immediately.
I applied the license key to the wrong Ingate serial - can I change it? a.k.a. Can I migrate a license from my Ingate XX to my VM?
No - once a license key is consumed, it is bound to a serial number in a one way process, whether or not you have yet installed the license file on your unit. Please check carefully to which unit serial you bind your license.
I lost the license file but have not applied it yet - can I get a new one?
Yes - enter the license code you originally received and you can download the same license file again.
Does the Ingate support video and would there be any licensing and capacity implications we need to consider?
Video is just another media stream to handle in Ingate (m= lines in the SDP). Ensure that your system does in fact use SIP as the signaling protocol. Our licensing is based per stream i.e. for a video call there will be 2 media licenses taken; 1 for the audio stream and 1 for the video. So you will need to take this into account.
*Check your bandwith requirements since video will add a at least a 1 Mbit per call, per direction.
Administration Problems
Apply Configuration
-
Why is the connection to my firewall/SIParator® broken when I apply the configuration?
Why is the connection to my firewall/SIParator® broken when I apply the configuration?
Problem description
When a new configuration is applied, the
connection to the firewall is lost for a short period (1-3
minutes). After that, a page is displayed which informs that the time
limited testing was autmatically aborted.
What to do
Some settings in the new configuration applied
makes the firewall unable to receive configuration from your
computer. This could be a changed IP address of the firewall, change
of configuration computers (on the Access Control page) or
something else.
To make sure that everything is correct, do like this:
- Go to the Save/Load Configuration page and press the
Abort all edits button. This will make all settings in the web
interface to adapt the values which the firewall is currently using in
the permanent configuration.
- Re-enter the settings which you tried to apply.
- Apply the new configuration.
When changing the IP address of the firewall to which configuration
is sent (the address you direct your web browser to), you have to
direct your web browser to the new IP address when you have pressed
Apply configuration, to reconnect to the firewall.
Upgrade Problems
-
I can't log on to the upgrade web system on this web site.
-
Do I have to reboot my Ingate unit when I upgrade?
-
Do I have to run the latest version on my Ingate Firewall/SIParator®?
I can't log on to the upgrade web system on this web site.
Problem description
When I try to log on the web system to get an upgrade, I
type in the correct username and password, but I still don't get
logged on.
Solution
The Ingate upgrade web system uses cookies for the
login. You must enable cookies in your web browser to log on properly.
Do I have to reboot my Ingate unit when I upgrade?
There will be an automatic reboot and a corresponding
break in the network traffic when you upgrade. If SIP, dynamic session
control or NAT is used, all these sessions will be torn down as the unit reboots.
Do I have to run the latest version on my Ingate Firewall/SIParator®?
You don't necessarily have to run the latest software version. Your
firewall/SIParator® will work with older versions, too. However,
in almost every new version, there are security fixes for possible
exploits in the older version, which means that from a security point
of view, you should always upgrade.
When you run into problems with your unit, you should start with
trying to upgrade, as there are a lot of bug fixes in all new
versions. Probably, you won't need to contact our support, but the
problem is already fixed in a newer software version. The logging is
also improved, which means that you can often find the cause of the
problem yourself from reading the log.
SIP Problems
-
Do Ingate products support Call Hold, Call Transfer, Call Waiting and other call features?
-
How do I use RADIUS Accounting with Ingate Firewall/SIParator?
Do Ingate products support Call Hold, Call Transfer, Call Waiting and other call features?
The Hold and Transfer features are usually implemented on the
client side. The Ingate box has no special support for this, as it is
part of the standard SIP signaling, which the Ingate box forwards
anyway.
The Call waiting feature is sometimes implemented in the server
instead of the client. The Ingate box has no such feature, but will
forward any signaling for clients implementing this.
There are no extra settings for these functions; the settings
allowing normal calls to be successfully set up should be enough,
provided that the features themselves are implemented in the
clients.
How do I use RADIUS Accounting with Ingate Firewall/SIParator?
This is how to configure your firewall/SIParator to use RADIUS Accounting
for calls to or from local users. If you are only interested in accounting for calls through the
firewall/SIParator, you only have to turn the RADIUS Accounting on. If you also want to bill for calls where both clients are on the same side,
you will have to force the users to go via the firewall. For this, the firewall will have to act as a
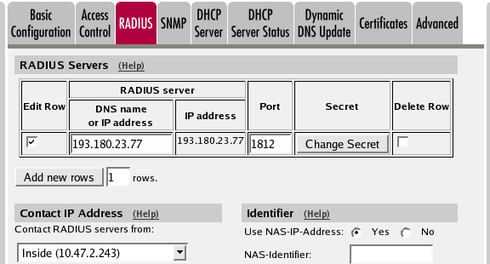
back-to-back user agent (B2BUA) for all calls. This feature is only available when the SIP Trunking module or Advanced SIP Routing module has been installed. First, define the RADIUS server to receive accounting
ticks. This is done on the RADIUS
page. If the RADIUS server should only be used for accounting, you can
enter any port number in the table. The firewall will use port 1813
for accounting. If you use the firewall as the SIP registrar, and the
RADIUS server should be used for SIP authentication as well, you need
to enter the port number on which the RADIUS server listens for
authentication requests (usually ports 1812 or 1645). Define a local SIP domain. This can be any domain name
you like, as long as it isn't an existing domain somewhere else. A
good choice is to use your company www domain, but replace the "www"
with "sip", like sip.ingate.com. The same domain
can also be used in pure SIP-to-SIP calls. This domain should be entered on the
User Database page under
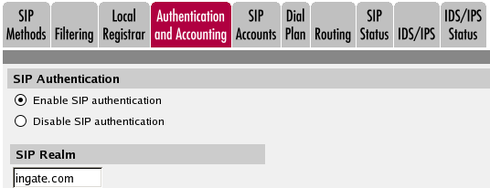
SIP Traffic. Go to the Authentication and Accounting page and turn
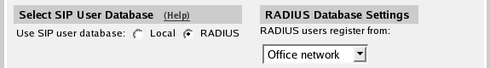
authentication on. Also enter your SIP domain as the Realm. If the firewall should be used as registrar, you select to use
the RADIUS user database for SIP users and also select which network
the SIP users can register from. On the Dial Plan page, you define how calls
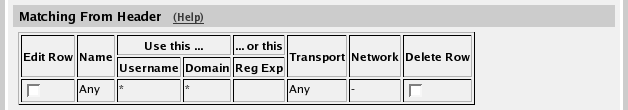
should be routed through the firewall. First, turn the Dial Plan on. In the Matching From Header table, you define from which
network the calls can come. You can also select what the From header
(that tells who is calling) should look like. This is used when
matching requests in the Dial Plan table below. For
this example, you only need one criterion to match on; all calls
should be treated the same, regardless of origin. In the Matching Request-URI table, you define call
destinations. This is used when matching requests in the
Dial Plan table below. In this case, you want to define a Reg Exp
(regular expression) which matches all Request-URIs. Enter "(.+)@(.+)"
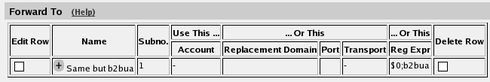
in the Reg Exp field. In the Forward To table, you define where
calls should be forwarded. This is used in the
Dial Plan table below. In this case, the calls should be forwarded to their original
destination, but the firewall should forward them as a B2BUA. Enter
"$0;b2bua" in the Reg Exp field. This will reuse the incoming
Request-URI, but make the firewall act as a B2BUA instead of a
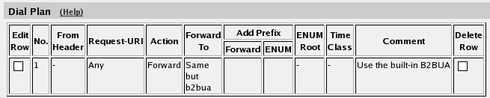
proxy. At last, you combine these definitions in the
Dial Plan table. Make a new row in the table and
select the definitions from the tables above. Now, when a SIP user calls another SIP user, the firewall will
step in and always stay in the path for the call. Both SIP clients
will signal to the firewall only, and the firewall will forward
signaling and media between them. Finally, go to the Save/Load Configuration page under
Administration and apply the new settings by pressing
Apply configuration.
VPN Problems
-
How do I configure my VPN client to work with an Ingate
Firewall/SIParator®?
-
I can't get a PPTP connection to my firewall.
How do I configure my VPN client to work with an Ingate
Firewall/SIParator®?
Here is information on how to configure various VPN
clients to connect to an Ingate Firewall/SIParator®.
I can't get a PPTP connection to my firewall.
Problem description
When the PPTP client tries to connect, the connection
is never established.
1. Check that the user is enabled
Log on to the GUI and press the VPN
button. Go to the PPTP page and make sure that the PPTP user is
set to On in the PPTP Users table. Go to the
Save/Load Configuration page under Administration and
apply the new setting.
2. I did that, but it still doesn't work
The most probable reason is that the GRE packets are blocked
somewhere between the client and the firewall. Use the packet capture
on the firewall and some sniffer (like Wireshark) on the
client to check that GRE packets are really sent and received in both
directions.
If packets are sent, but never received, you must ask your network
provider to let GRE traffic through.
Media Problems
-
Does the Ingate SBC do transcoding?
-
I hear audio artifacts - there is crackle / hiss / humm / pop / clicking / noise etc on the line.
-
My audio suffers from packet loss/jitter/disorder.
Does the Ingate SBC do transcoding?
No. Between audio CODECs, currently no transcoding is possible. Between DTMF (in-band or out-of-band), currently no transcoding is possible. Between cleartext and encrypted, the SBC un/wraps (transcodes) where it is configured to do so.
I hear audio artifacts - there is crackle / hiss / humm / pop / clicking / noise etc on the line.
No audio transcoding is performed on the Ingate SBC, so any audio artifacts in your call audio are the result of bad or disrupted encoding at your ITSP or PBX.
My audio suffers from packet loss/jitter/disorder.
The Ingate SBC either forwards stream packets related to a call, or it silently drops them. Packet loss/jitter/disorder is generally attributable to overloaded or badly configured routers on the media path.
Traffic Problems
-
Why does my firewall reply to pings sent to its inside IP address when
I ping from the Internet, even though there are no firewall rules to
allow ping through the firewall?
-
Why can't I access my DMZ from the outside?
-
Why can't I access my web server/email server from the inside via my relay?
-
Why doesn't my Ingate Firewall receive packets sent to one of its relays?
-
Why does my firewall reply to pings sent to its inside IP address when
I ping from the Internet, even though there are no firewall rules to
allow ping through the firewall?
-
Why is some web/e-mail traffic rejected, even though I opened for all
such traffic?
Why does my firewall reply to pings sent to its inside IP address when
I ping from the Internet, even though there are no firewall rules to
allow ping through the firewall?
Problem description
My firewall has a public IP address on the outside
interface and a private IP address on the inside interface. If I try
to ping the inside IP address from a computer located outside the
firewall, it replies to ping even when no firewall rules have been set
up.
Explanation
Rules in the firewall only affect traffic addressed
through the firewall, not traffic to the firewall. The
firewall always listens for traffic to all its IP addresses on all
interfaces. It replies to ping in the described manner because the
setting Policy For Ping to Your Ingate Firewall is set to
Reply to ping to all IP addresses. If you want the outside
interface to only reply to ping to the public outside IP address, you
should change the setting into Only reply to ping to the same
interface. If you don't want the firewall to reply to ping at all,
select Never reply to ping.
Why can't I access my DMZ from the outside?
Problem description
The public IP addresses you received from your
ISP were divided into two groups, one of which is used on your DMZ and
one on the outside of the firewall. When this configuration is
applied, the DMZ computers can't be accessed from the outside.
What to do
The probable cause to this is that the router
acting as default gateway for the firewall doesn't know that the DMZ
IP addresses should be routed through the firewall. Contact your ISP
for reconfiguration of the router.
Why can't I access my web server/email server from the inside via my relay?
Problem description
On the firewall, there is a relay forwarding
packets from the outside to a server on the inside or on a DMZ. This
works from the outside, but I can't access the server from the inside
using the public IP or the server name.
What to do
The probable cause to this is that you haven't
allowed the computers on the office network to use the relay. Do
this:
- Go to the Networks and Computers page under Network
and create a network which contains both the Internet and
the office network. In some cases, you might already have such a
network. To create it, create a new row with two groups in it. Select
the Internet and the office network as subgroups (you probably have
them as networks already). Select "-" as Interface/VLAN for both,
and enter no IP addresses.
- Go to the Relays page under Rules and Relays and
find out which relay handles the traffic you have problems
with. Change Allow access from for this relay to the network
you just created.
- Go to the Save/Load Configuration page under
Administration and apply the changes.
Why doesn't my Ingate Firewall receive packets sent to one of its relays?
Problem description
A server was placed directly connected to the
Internet, but now the firewall is moved in between. This has resulted
in packets not arriving to the IP address formerly used for this
server, now for the firewall.
What to do
The probable cause to this is that the router acting
as default gateway for the firewall locks the IP address to the MAC
address of the server. This is reset when the router times out or is
rebooted.
Why does my firewall reply to pings sent to its inside IP address when
I ping from the Internet, even though there are no firewall rules to
allow ping through the firewall?
Problem description
My firewall has a public IP address on the outside
interface and a private IP address on the inside interface. If I try
to ping the inside IP address from a computer located outside the
firewall, it replies to ping even when no firewall rules have been set
up.
Explanation
Rules in the firewall only affect traffic addressed
through the firewall, not traffic to the firewall. The
firewall always listens for traffic to all its IP addresses on all
interfaces. It replies to ping in the described manner because the
setting Policy For Ping to Your Ingate Firewall is set to
Reply to ping to all IP addresses. If you want the outside
interface to only reply to ping to the public outside IP address, you
should change the setting into Only reply to ping to the same
interface. If you don't want the firewall to reply to ping at all,
select Never reply to ping.
Why is some web/e-mail traffic rejected, even though I opened for all
such traffic?
Problem description
Look for this kind of sequence in the
log (shown with Show newest on top):
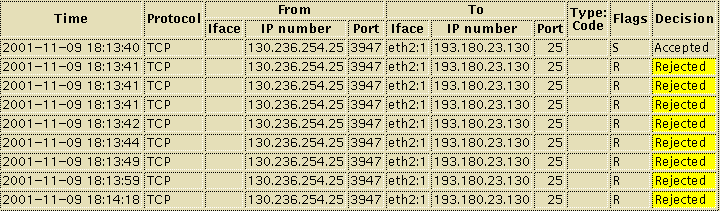
The significant sequence is an accepted S flag followed by rejected
R flags.
This is caused by the connecting software sending flags in an
inappropriate order. The Dynamic session management in the firewall
rejects flags which aren't in the correct order.
What to do
- Change to Packet filter for the affected services.
- Notify the sending server administrator about the defect
software.
Certificates
-
Why doesn't my TLS connection work?
Why doesn't my TLS connection work?
Problem description
TLS doesn't work with my firewall/SIParator™ even
though I made all the settings right.
What to do
Following is a simple check list to ensure that
all necessary steps were performed:
- Create a self signed certificate on the Certificates page.
- Select this certificate on the SIP Encryption page.
- Restart the firewall/SIParator™.
- Download the self signed certificate and import it on the
client machine. On a Windows computer, this is done using Internet
Explorer. Select Tools->Internet Options->Content->Certificate and
import it as a Trusted Root Certificate.
If it still doesn't work, check these
things:
- Check the time on the firewall/SIParator™ and the client
machine. The certificate is only valid in a certain time frame.
- Checking the event log of the Windows computer can be
helpful. Often the reason for the failure is stated there.
- The Common Name of the firewall/SIParator™ certificate
should point to one of its interfaces, preferably the outside. It is
important that the same address (ip or hostname) is used as the
outbound proxy setting in Messenger or it won't work.
Virtual Machines
-
Why does my VM keep losing its config? aka Why does my VM reset when I ping it?
Why does my VM keep losing its config? aka Why does my VM reset when I ping it?
Problem description
When you ping your VM, the config resets somehow. When you reboot your VM, the config resets somehow.
What to do
Eject or detach the Ingate installation ISO from the VM. Booting with the ISO attached is synonymous to a password reset
|